I don’t put tape over my webcams, neither on my MacBooks, iOS Devices nor on my Windows machines. I refuse to be like that. If someone was honestly suspecting a malicious attacker would spy on them using their webcam, then I would argue that these people, if they were consistent, would also need to rip out the microphones of their devices.
On the other hand, I’m not that naive to think that there is no risk involved using such input devices.
So I came to these, in my opinion, very sensible solutions:
On my MacBook I trust a combination of the hardware indicator LED of the Webcam in combination with Micro Snitch.
On iOS Devices I trust Apple’s sandboxing.
In Windows I found this solution sufficient for my needs:
I installed the Windows Device Console (devcon.exe). It is included in the Windows Driver Kit (WDK), but can also be found online on it’s own. Then I wrote three absolutely tiny batch files:
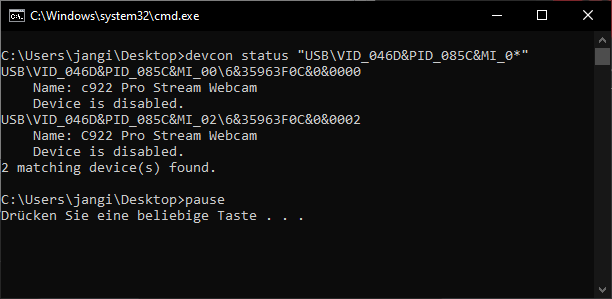
Check the status of the webcam:
devcon status "USB\VID_046D&PID_085C&MI_0*"
pause
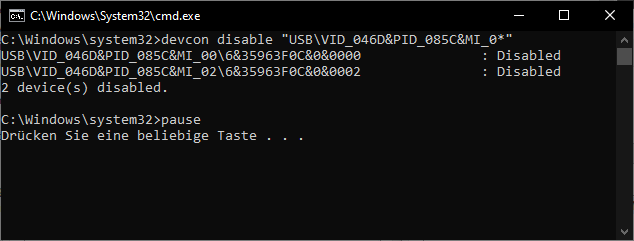
Disable the webcam:
devcon disable "USB\VID_046D&PID_085C&MI_0*"
pause
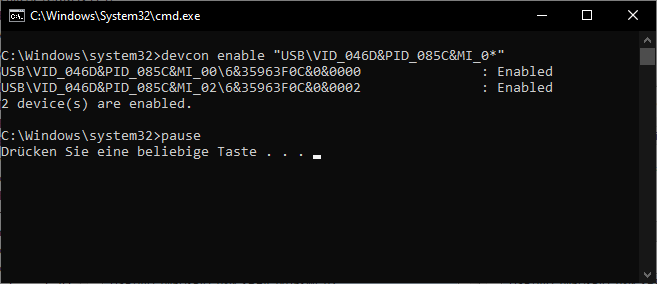
Enable the webcam:
devcon enable "USB\VID_046D&PID_085C&MI_0*"
pause
Both disable and enable need to be run as Administrator.
The hardware IDs can easily be found in device manager. My webcam has two hardware IDs, one for the ccd and one for the microphone.
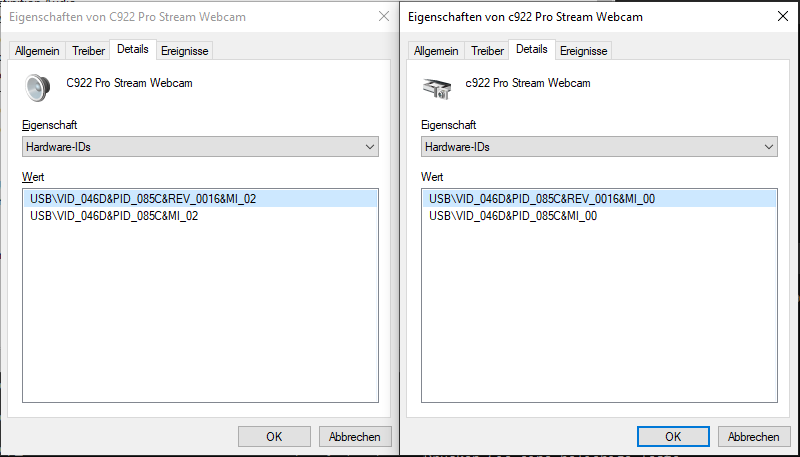
In my batch file I used an asterisk in place of the last digit to get both of them with the command.
Also, since I attached the webcam to my monitor’s integrated hub, it doesn’t get power when the monitor is powered off or in sleep mode (if it actually falls asleep).